Offering increased access to care, a vast array of options for obtaining it, and the ability for companies to increase productivity while decreasing costs, mhealth is transforming the way healthcare is delivered throughout the world. By following a few best practices, you can help to ensure that the security risks that come along for the ride won’t put your organization at risk.
Both a beauty and a beast, mHealth possesses a vast potential to meet a wide array of healthcare needs – and to make organizations vulnerable to risks they never dreamed of. It’s why every healthcare organization that envisions the benefits of mHealth must also be aware of associated risks to ensure proper implementation of appropriate security measures.
Various mobile security best practices include protection of an organization’s network infrastructure, the devices that it provides, and the sensitive data it possesses. In order to address the security issues that mHealth may present, experts recommend some combination of all three. Such best practices include the following – and will help your organization provide optimal quality of care within the most secure environment possible.
1. Strike a balance.
One of the questions that plagues healthcare leaders and IT officers is: “How do we decide who gets what data on what devices?” If it were up to the IT department, all devices and the data within would be locked down both physically and virtually. And if it were up to the organizational innovators and thought leaders, there’d be free rein to implement and expand the potential for transformation that mobile computing offers.
Somewhere between the extremes, there lies a balance that meets the needs of stakeholders to experience both optimal security and optimal functionality, though opinions vary regarding what comprises such a solution. Regardless, there are three key ingredients to the mix, and many feel the most comprehensive solution is a blending of all three:
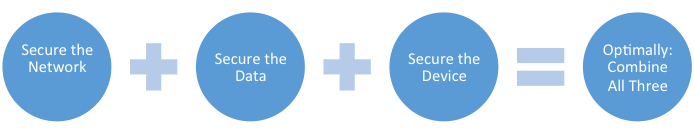
Comprehensive Mobile Security Solution
The best framework for a solid and secure mobility system incorporates the organization’s business mission and objectives in a comprehensive mobility plan that includes network, data and device security all wrapped into one. Typically, this will be comprised of various combinations of Mobile Application Management (MAM), data encryption that includes Virtual Privacy Network (VPN) access, and Mobile Device Management (MDM).
2. Make it clear and make it mandatory.
Mobile security software should never be a “nice to have”, but an essential part of ensuring that your employees are helping to keep data safe. Mobile computers are a wonderful addition to your company’s productivity arsenal - armed with enough portable muscle to accomplish great things.
However they’re also quite capable of inflicting enormous amounts of damage if the sensitive data that passes through them is not appropriately secured. Unprotected mobile devices are epidemic across the globe, with Android devices being some of the most vulnerable. That’s why experts recommend implementing third-party software policies that include mandatory mobile security software and discouraging the downloading of hazardous third-party apps.
3. Tighten the talk.
Wireless communications are incredibly easy to intercept, so experts recommend encryption for all mobile communications. In addition, if such a device is going to connect to a company or cloud-based system, the best access door should be through a Virtual Privacy Network (VPN). This arrangement provides strong encryption, as well as tracking, managing and authenticating of users who are accessing the system from mobile devices.
4. Make authentication iron-clad.
There are local security mechanisms that are frequently used for mobile devices, such as biometrics that are built into the hardware – but experts recommend that multiple layers of authentication be used to prevent access to critical systems and information. And users should always have strong passwords enabled on sensitive data access points on devices - with the ability for the company to wipe the device’s internal storage if numerous erroneous access attempts are detected.
5. Invite intruders.
A reputable security firm should be hired to help with regular mobile audits, which should include penetration testing on mobile devices in use. Such firms can also help with correcting issues that are discovered. According to CIO, “Hire the pros to do unto your mobile devices what the bad guys will try to do unto you sooner or later, and you’ll be able to protect yourself from the kinds of threats they can present.”
Without a doubt, mhealth is changing the healthcare ecosystem. Offering increased access to care, a vast array of options for obtaining it, and the ability for companies to increase productivity while decreasing costs, this mobile giant will continue to transform the way healthcare is delivered throughout the world.
Inherent to such rampant growth is always some measure of risk – and where mHealth is concerned, that risk rears its ugly head in the security issues that reside within. But by following best practices for mobile health security in your organization, you can tame the security beast, and let the beauty of mHealth shine.
Log in or register for FREE for full access to ALL site features
As a member of the nuviun community, you can benefit from:
- 24/7 unlimited access to the content library
- Full access to the company and people directories
- Unlimited discussion and commenting privileges
- Your own searchable professional profile






.jpg)
